Mobile Malware Sets to Ruin Your Holidays…
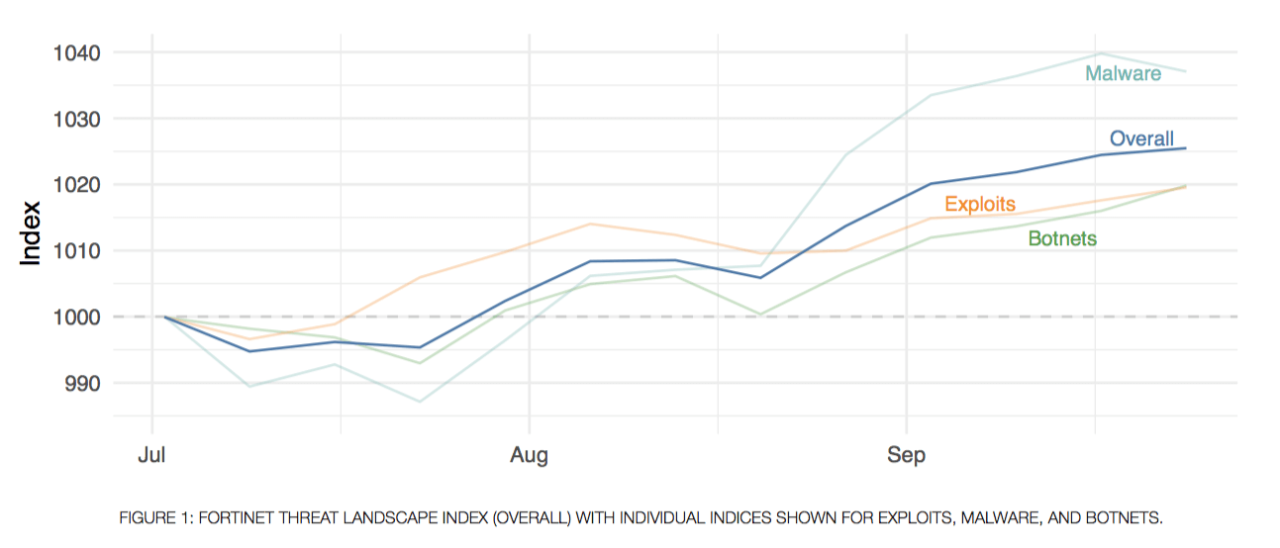
Fortinet has just released its global Threat Landscape Report for Q3 of 2018, analyzing threat data culled from millions of Fortinet devices deployed across the globe. One of the unique aspects to this report is that we provide a regular analysis of the threat landscape, rather than the annual or semi-annual formats provided elsewhere. This allows us to dig a bit deeper into what is happening across exploits, malware, and botnets, with deeper dive indices to provide cybersecurity professionals with timely information on issues they should be concerned with right now, rather than with a recap long after events have taken place.
It also provides us with the opportunity to deliver a running analysis of trends. Like any other sort of security strategy, identifying patterns helps cybersecurity professionals get out in front of threats rather than simply reacting to them. Of course, even a quarterly report isn’t enough. Our FortiGuard Labs Weekly Threat Brief provides timely insight and analysis that help organizations see and respond to breaking threats and trends. And for near real-time information, organizations can subscribe to our FortiGuard Threat Intelligence services that provides live threat updates, hot bulletins on breaking threats, and real-time software updates to Fortinet security solutions.
One of the most interesting aspects of producing the quarterly Threat Landscape Report is that we are able to uncover some critical trends that might be missed when looking at risk on a minute-by-minute basis. This quarter has been no different. Below are trends highlighted in the Q3 report that bear emphasizing.
Cryptojacking creates a threat gateway
Over the past year or so we have seen cryptojacking increase as the top security concern. This is reflected in the fact that during 2018, the number of platforms used to mine data jumped 38%. Even more concerning, however, is that people are beginning to realize that cryptojacking is more than simply a drain on system performance and resources. We have begun to see a rise in cryptojacking variants that disable existing security solutions such as antivirus, open additional communications ports on deployed firewalls, and add administrator accounts that enable attackers to return to propagate new malware. The result is that a cryptojacking infection doesn’t just steal CPU cycles, but is also creating a gateway for additional exploits.
Mobile devices are a growing threat
Threats from mobile devices are having a bigger impact on network security. During Q3, more than a quarter of organizations experienced a mobile malware attack. Android OS for mobile devices is far and away the top culprit. By comparison, only .0003% of threats were attributable to Apple iOS. In fact, 14% of malware alerts this past quarter were Android related. This isn’t just mobile device alerts. It’s 14% of all malware. Security leaders without a strategy to address mobile threats, especially those with an open BYOD policy, are making their organizations extremely vulnerable as mobile devices are increasingly an entry point into corporate assets.
Botnets persist longer than ever
While the number of botnet infections didn’t climb appreciably during Q3, the number of days that an botnet infection was able to persist inside an organization increased 34% from 7.6 days to 10.2 days. This indicates that botnets are becoming more sophisticated, difficult to detect, and harder to remove. However, this increase is also the result of many organizations still failing to practice good cyber hygiene, including patching and updating vulnerable devices. In addition to implementing best security practices, organizations need to adopt tools like FortiNAC Network Access Control to see, segment, and track every device on the network, including IoT devices, and augment those efforts with Fortinet’s Security Rating solution that is designed to find the weaknesses and vulnerabilities within your environment and provides actionable recommendations. This solution needs to be applied before an outbreak to prevent exploits, and after an event to ensure that post-event clean-up has been thorough enough.
Data encryption has set a new bar
Based on our analysis, for the first time ever encrypted traffic now represents over 72% of all network traffic. That’s a nearly 20% increase in a single year, up from 55% in Q3 of 2017. While many folks see the growth of encryption as a good thing for security, higher encryption rates also present serious challenges to threat monitoring and detection. Many cyberattacks use encrypted communications for cover, knowing that critical performance limitations inherent in nearly all Firewall and IPS devices continue to restrict an organization’s ability to inspect encrypted data without seriously impacting network performance. On average, the performance hit for deep packet inspection is a whopping 70%, rendering them nearly useless in networks where performance is critical.
This is why most security vendors don’t publish their SSL inspection numbers, and why much of today’s encrypted traffic is simply not analyzed for malicious activity—making it an ideal mechanism for criminals to spread malware or exfiltrate data. To address this challenge, Fortinet has developed custom security processors designed to accelerate the inspection of SSL traffic. As a result, FortiGate solutions are consistently rated as the highest performing encryption inspection solutions on the market. With a performance impact of less than 15%, FortiGate appliances are one of the only solutions able to perform deep packet inspection at network speeds.
Addressing the Challenge
- To successfully address today’s challenges, IT teams need to rethink their security strategies. This includes: Automating security hygiene strategies, such as patching and updating, configuration analysis, log analysis, and identifying and monitoring connected devices. Automation allows organizations to realign limited human resources to higher order security functions.
- Deploying FortiGate NGFW solutions with purpose-built security processors that enable the inspection of encrypted traffic at network speeds. Our third-party tested and certified devices provide the fastest encryption inspection on the market, hands down.
- Implementing an integrated Fortinet Security Fabric architecture that can seamlessly span the entire expanding attack surface, including Fortinet and third-party solutions, for unified visibility and centralized orchestration from a single console.
- Deploy FortiSandbox advanced sandboxing functionality across multiple security devices and environments, enabling you to prevent and detect previously unknown threats regardless of where they appear.
- Maintaining a comprehensive inventory of devices (especially IoT devices) across your network and baseline their behavior using FortiNAC. With this information in hand, you’re able to monitor for aberrant behavior that may reflect cryptojacking activity.
- Deploy 24/7 security and network operations that enable you to search for and find malware during the weekends and during holidays. FortiGuard threat research shows that as the volume of business-related traffic drops during non-operating hours, it is much easier to identify, track, and trace malicious traffic.
- Deploy appropriate controls to protect against mobile device threats, especially at your wireless access points. This requires that wireless access points, such as FortiAP, and mobile security services be fully integrated into your next-generation firewalls. This is even more effective when combined with the automated threat-intelligence sharing enabled by the Fortinet Security, including our third-generation FortiNAC Network Access Control solution.
As cybercriminals successfully target the growing number of attack vectors being implement due to digital transformation efforts, doing more of the same when it comes to security is a losing strategy. Threat advances outlined in Fortinet’s Q3 Threat Landscape Report indicates that organizations not only need to become more hypervigilant about security, but they also need to be smarter about what they do with that information. Those who fail to meet their digital transformation efforts with an equally aggressive security transformation strategy will forfeit their ability to compete in today’s digital marketplace as they become victims to the continually innovative cybercrime community.
Sign Up for Your FREE Cyber Threat Assessment Today!!! CLICK HERE