Why Organisations Need Cloud Access Security Broker – CASB
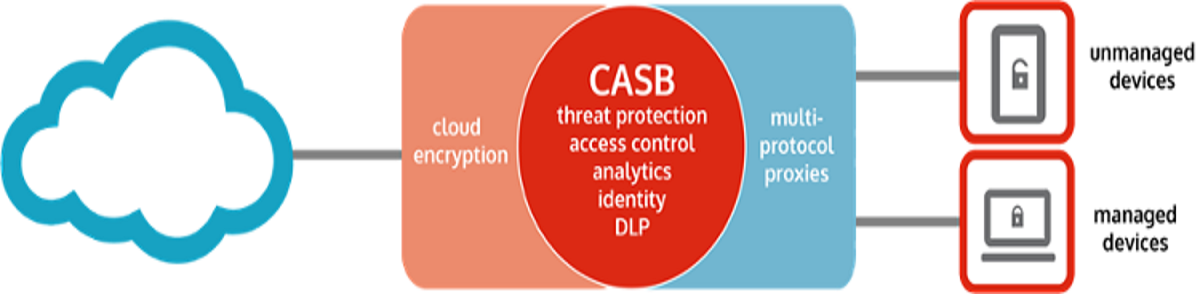
Lets face it, the cloud adoption is growing at an exponential pace, many traditional IT setups are being replaced and evolved to adopt cloud whether on a whole or as a hybrid solution. people are becoming increasingly mobile, collaborate more freely, and shifting more of their data to the cloud. With that in mind, organisations big or small needs security that governs use and protect data everywhere. Most IT teams are still struggling trying to make their legacy security products to continue providing a secured computing environment, only to fail as these products are not designed primarily to handle the modern cloud. Legacy solutions works like binary, on or off, allow or block, making exceptions or granular controls are not a standard in many legacy products. These products also present blind spots, putting sensitive data at risk of loss, exposure and abuse.
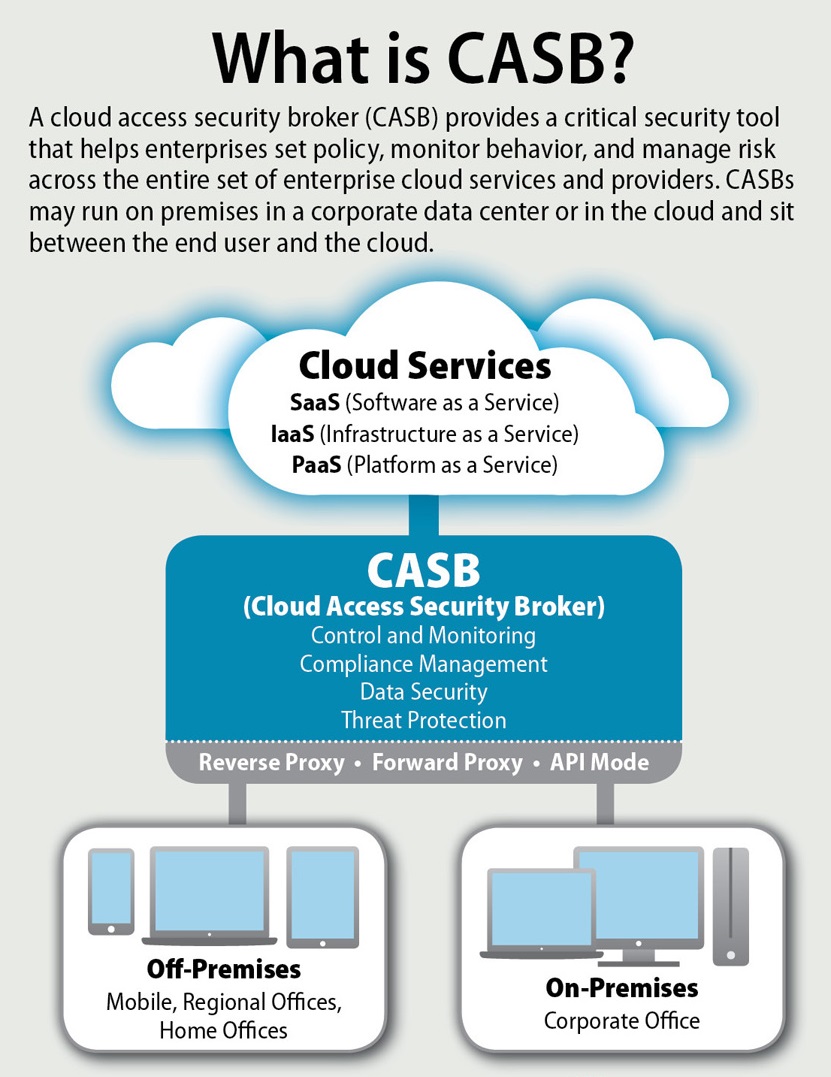
To optimize the adoption of cloud, people and companies should be able to collaborate without limits, working safely across the cloud, web, devices and locations. A good Cloud Access Security Broker (CASB) platform should provide the deepest visibility into cloud and web transactions so that IT security teams can make informed policy decisions to reduce risk. The platform should also enable enterprises to secure both sanctioned and unsanctioned cloud services, protect sensitive data across the cloud and web, and stop even the most advanced online threats. Essentially a good CASB solution should empower organisations to customize security designed according to how the company work, without slowing them down.
When considering which CASB solution you should adopt, you may want to look out for the following features:
- Blind Spot Elimination – Ability to understand all inputs (Logs, SaaS, IaaS, web) in extreme definition and performs big data analytics on details include user, group, location, device, service, destination, activity, and content in real time. This helps enterprises eliminate the blind spots legacy vendors can’t see and make policy enforcement simple across thousands of SaaS and IaaS services, and millions of websites.
- Guard Data Everywhere – Protect and guard sensitive data everywhere through DLP and encryption across SaaS, IaaS, and web. The solution should also be equipped with intelligence to reduce your inspection surface area and advanced DLP methods like exact match and fingerprinting to increase detection accuracy. Built in the cloud,with the ability to work regardless of location or device and handles the direct-to-cloud and direct-to-web traffic that others miss.
- Stop Elusive Attacks – Built-in advanced threat protection to stop elusive attacks across SaaS, IaaS, and web. Built in the cloud and packed with real-time and deep detection engines, with ability to find malware and ransomware that legacy tools miss. Proactive threat intelligence and powerful workflows to quarantine malicious files and reverse the effects of an attack.
- Full Control – SaaS, IaaS, and web security platform built from the start in one cloud that’s easy to use. Unlike cobbled-together tools, the CASB solution should eliminate policy conflict through standardized categories across SaaS, IaaS and web. Save your security team’s time by avoiding redundant DLP and threat protection configuration steps and having to switch from one tool to the next. A solution that is built on the cloud would also ensure that it scales automatically to meet your needs.
To Secure Your Cloud Today, Drop Us a Message HERE!!!

