Seven Steps to Securing the Public Cloud

Step 1: Learn your responsibilities
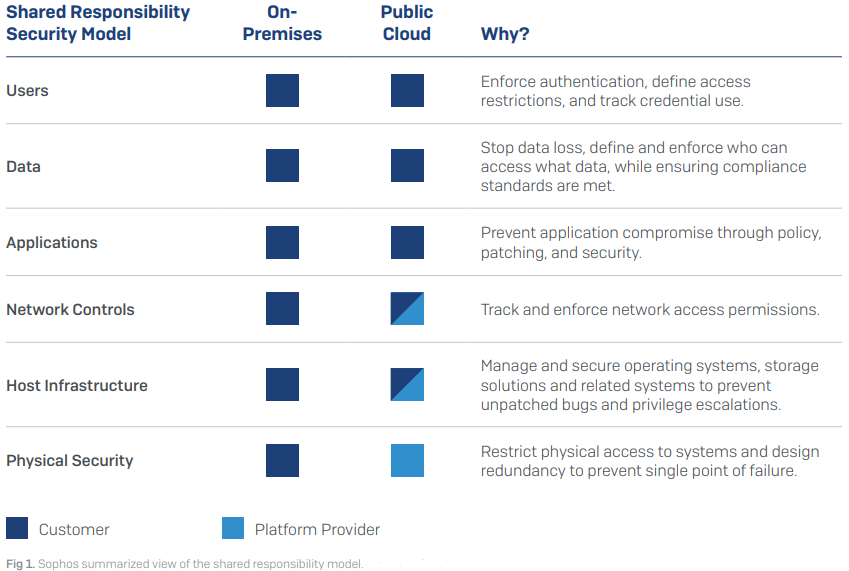
This may sound obvious, but security is handled a little differently in the cloud. Public cloud providers such as Amazon Web Services, Microsoft Azure, and Google Cloud Platform run a shared responsibility model – meaning they ensure the security of the cloud, while you are responsible for anything you place in the cloud. Aspects such as physical protection at the datacenter, virtual separation of customer data and environments – that’s all taken care of by the public cloud providers. You might get some basic firewall type rules to govern access to your environment. But if you don’t properly configure them – for instance, if you leave ports open to the entire world – then that’s on you. So you’ve got to learn your security responsibilities.
Step 2: Plan for multi-cloud
Multi-cloud is no longer a nice-to-have strategy. Rather, it’s become a musthave strategy. There are many reasons why you may want to use multiple clouds, such as availability, improved agility, or functionality. When planning your security strategy start with the assumption that you’ll run multi-cloud – if not now, at some point in the future. In this way you can future-proof your approach.
Think about how you will manage security, monitoring, and compliance across multiple cloud providers, in separate systems and consoles. The easier the management experience the easier it is to cut incident response times, increase threat detection, and reduce compliance audit headaches. Not to mention aiding retention of valuable team members. Look for agentless solutions that allow you to monitor multiple cloud provider environments within a single SaaS console, reducing the number of tools, time, and people needed to manage security across multiple cloud accounts and regions.
Step 3: See everything
If you can’t see it, you can’t secure it. That’s why one of the biggest barriers to getting your security posture right is getting accurate visibility of your infrastructure. Take advantage of tools that provide a real-time visualization of network topology and traffic flow, with a full inventory breakdown including hosts, networks, user accounts, storage services, containers, and serverless functions.
For enhanced visibility, look for tools able to identify potential vulnerabilities within your architecture so you can prevent a potential breach point. Potential risk areas include:
- Databases with ports open to the public internet that could allow attackers to access them
- Public Amazon S3 Simple Storage Services
- Suspicious user login behaviors and API calls – such as multiple logins to the same account at the same time, or a user logging in from different parts of the world on the same day
Step 4: Integrate compliance into daily processes
Moving workloads to the cloud introduces the challenge of meeting compliance regulations across a more distributed network, often involving regular development releases. To ensure
compliance, you need to create accurate inventory reports and network diagrams of your cloud footprint, and ensure your compliance checklist is met in a dynamic environment.
When it comes to meeting audit deadlines, often organizations fall back on the short-term fix of diverting resources from profitable business projects. Yet this is not sustainable longer term and, as daily snapshots quickly become obsolete, this doesn’t provide the continuous compliance monitoring needed for standards such as ISO 27001, HIPAA, and GDPR.
Look for solutions that allow you to raise compliance standards without added headcount by providing real-time snapshots of your network topology, and automatically detecting changes to your cloud environments in real time. You’ll also want the option to customize policy to meet the specific needs of your sector or vertical.
Of course, reporting is only one aspect of compliance. You also need to be able to address compliance failures. The challenge is that it is often hard to get the right people in operations, development, and compliance to work together due to lack of effective collaboration channels.
To make the process of addressing compliance failures run smoothly, find solutions that integrate with your existing ticketing solutions, including alert information that can be used to create, assign, and track issues to completion, ensuring important tasks are never lost, even during a release.
Step 5: Automate your security controls
The ability to automate processes is one of the joys of DevOps. But, just as your teams enjoy automating deployment of infrastructure templates and scripts, saving hours of development time, so you should also consider what security controls you can automate.
In the collaborative framework of DevOps, security is a shared responsibility, integrated from end-to-end. This mindset led to the coining of the term “DevSecOps,” emphasizing the need to build strong security foundations into DevOps initiatives.
The need for automated security is clear as cybercriminals increasingly take advantage of automation themselves in their attacks – for example, using stolen user credentials to automate provisioning of instances for activities such as cryptojacking, changing account settings, or revoking legitimate users to avoid detection. Indeed, the canvassing of cloud environments for vulnerabilities in passwords, security group settings, and code are now commonplace.
The two main reasons why attacks on public cloud environments succeed are that the architecture configuration is not secure, and that threat response hasn’t kept pace with attackers. Automation of security controls is key to addressing these issues:
To ensure the security of your public cloud environments, look for a solution that can:
- Auto-remediate user access vulnerabilities and resources, with ingress from any source on any port
- Identify suspicious console login events and API calls that suggest shared or stolen user credentials are being used by an attacker
- Report anomalies in outbound traffic to alert your organization to activities such as cryptojacking or the exfiltration of data
- Reveal hidden application workloads from the behavior of the host computer instance to highlight hidden exposure points (e.g. databases)
Step 6: Secure ALL your environments (including dev and QA)
While the public cloud data breaches that made headlines tend to be those that hit an organization’s production cloud environment (the one your customers use), attackers are just as likely to come after your computing power – on your development and QA environments – for activities like cryptojacking.
You need a solution that can secure your all environments (production, development, and QA) both reactively and proactively. The solution should be able to ingest your activity logs (for example, VPC Flow logs and CloudTrail logs) to identify issues that have already occurred, such as when an undesired port is open in the firewall. At the same time, the solution should be able to proactively scan Infrastructure-as-Code (IaC) templates from your repositories like GitHub and integrate with your CI/CD pipeline tools such as Jenkins. This ensures that vulnerabilities introduced into code are detected long before it’s rolled out to your servers – preventing a nasty news headline.
Step 7: Apply your on-premises security learnings
This may sound odd in a public cloud guide, but on-premises security is the result of decades of experience and research. When it comes to securing your cloudbased servers against infection and data loss, start by thinking about what you already do for your traditional infrastructure, and adapt it for the cloud:
Next-gen firewall: Stop threats from getting onto your cloud-based servers in the first place by putting a web application firewall (WAF) at your cloud gateway. Also look to include IPS (to help with compliance) and outbound content control to protect your servers/VDI.
Server protection: Run effective cybersecurity protection on your cloud-based servers, just as you would your physical servers.
Endpoint protection: While your network may be in the cloud, your laptops and other devices are staying on the ground, and all it takes a phishing email or spyware to steal
user credentials for you cloud accounts. Ensure you keep endpoint and email security up to date on your devices to prevent unauthorized access to cloud accounts.
Stay tuned on our next article to see how you could apply these seven steps with a single solution….
*Article taken from Sophos White Paper on Securing Public Cloud